Page 2 of 7
Request Exploit
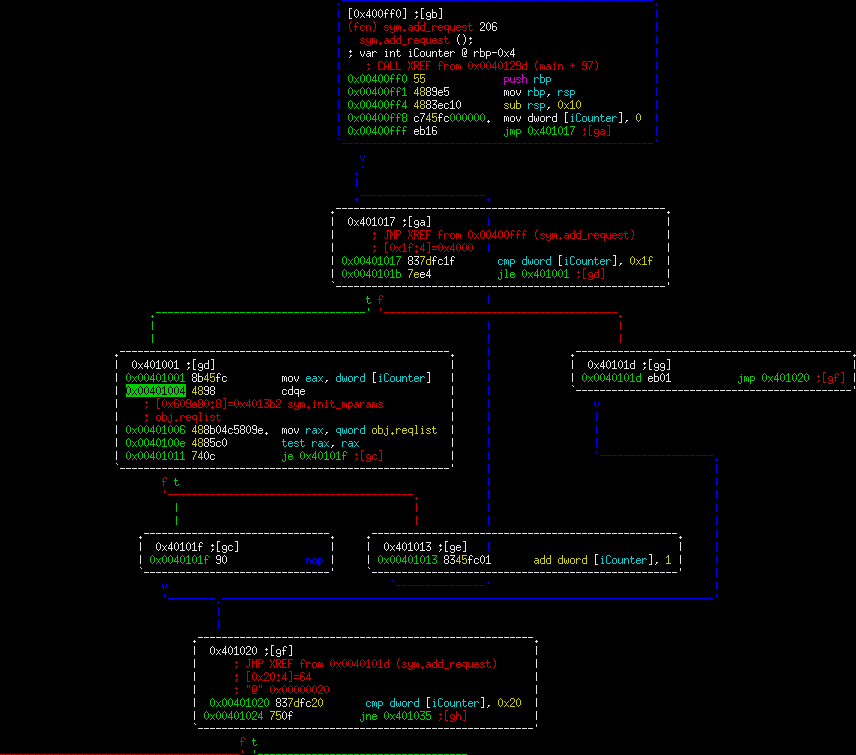
In this first part, we can tell there's a global named "reqlist". It is being iterated over 32 times looking for an entry with 0. Basic idea here is that this program will fill in holes in the global array with something (likely pointers). Let's look at the next part.
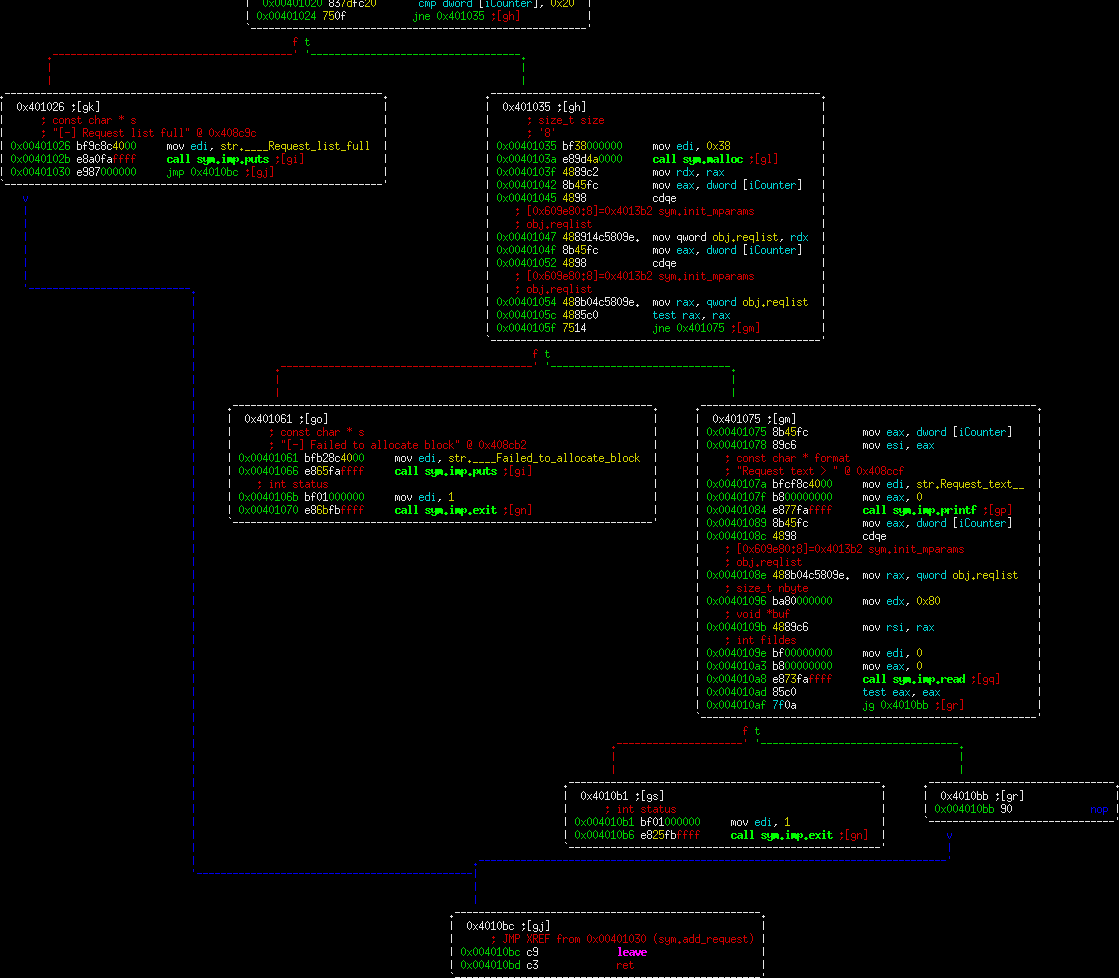
This is where it gets interesting. We're making a call to malloc in block 0x401035 for 0x38 bytes. Then in the very next block we're asking for input from the user, reading into this block 0x80 bytes. So this is effectively a blatant heap overflow. However, the question is how you turn that into an exploit. This function by itself would be difficult to fully exploit since you're going to be overwriting the wilderness value if you use the overwrite here. Let's keep looking.