Arbitrary Read
Having an arbitrary read allows you to not have to guess on your exploits. With a minimal arbitrary read you should be able to fully remove randomization from almost any binary. I spent a while looking for memory leaks and I found a few.
Heap Address Leak
This was already mentioned in the edit memo section. It's blatant, and it allows you to know exactly where the heap is.
Arbitrary Read
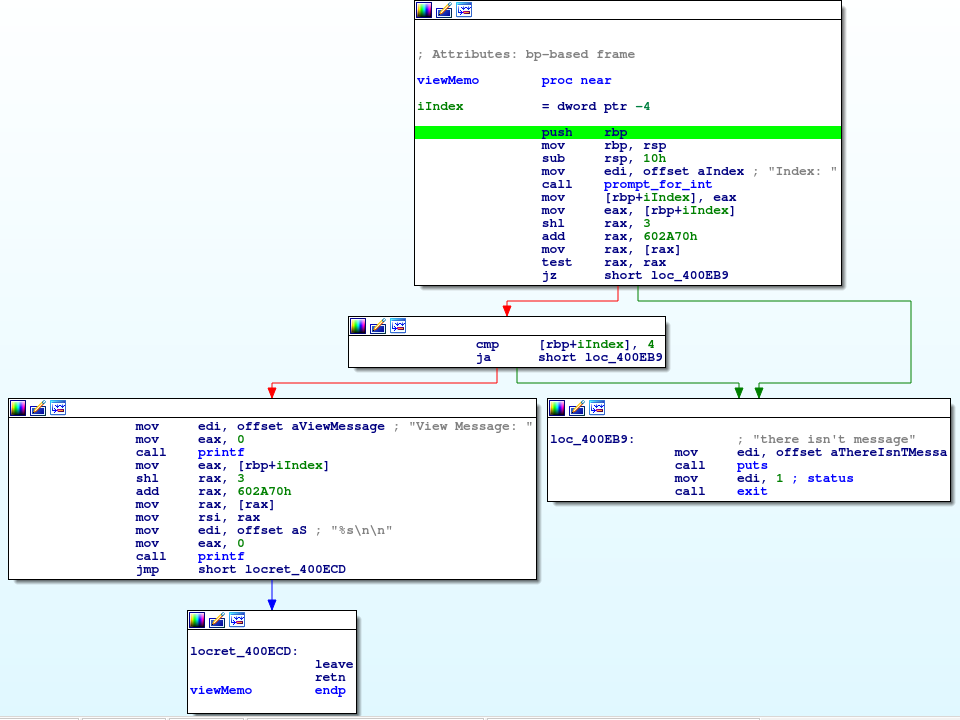
So view memo shows us the heap address by default. However, since we have an arbitrary write and it's reading the address to print from the global variable section, we have the ability to mess with that and cause it to print whatever we want. The view memo code is as follows:
We can see that it simply dereferences the index that we give it, and prints it as a string. The dereference happens at a static global offset that we control, and we have an arbitrary write. This makes an easy arbitrary read now:
- Use arbitrary write to write the address we want to leak at the global address of the pointers array (0x602A70)
- Use the view memo option with an index of 0 when prompted
- Profit
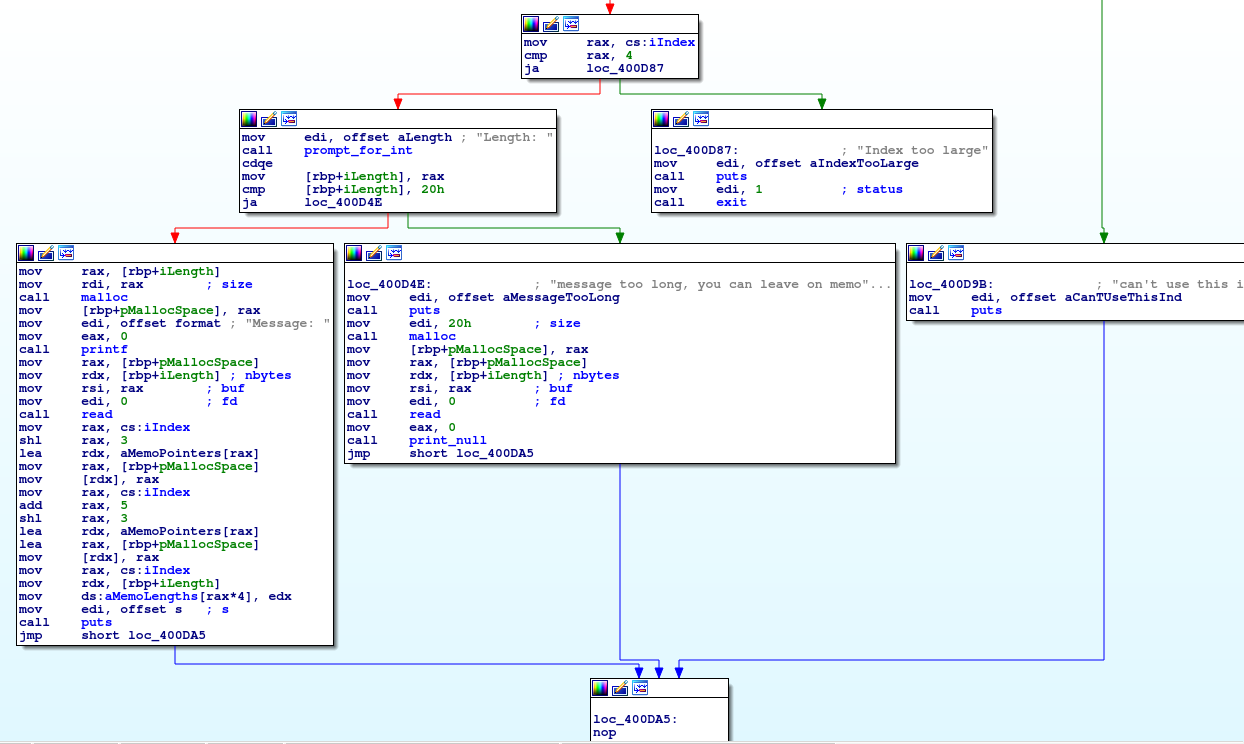
There's one little problem still though. While we have an arbitrary read and should theoretically be able to determine the stack location using that, pwntools wasn't working correctly at the time... Luckily for me, there's a strange behavior that I mentioned in the leave message section where it actually writes a stack pointer address to a global variable. This behavior in general is odd. Stack variables are local. If the goal was to keep track of a local pointer, well you already have it. Placing that pointer into global space just gives attackers the ability to de-randomize the stack address.
Notice in the far left block at the bottom, we load the address of a stack variable. We then save it into the memo pointers array. At this point, all we have to do to leak the stack address is:
- Write a memo of size 32 (or less)
- Use arbitrary read to read the pointer value off of the global pointers variable
We now have a pretty good idea of where everything is on a fully randomized binary. Time to exploit.