Headerquery
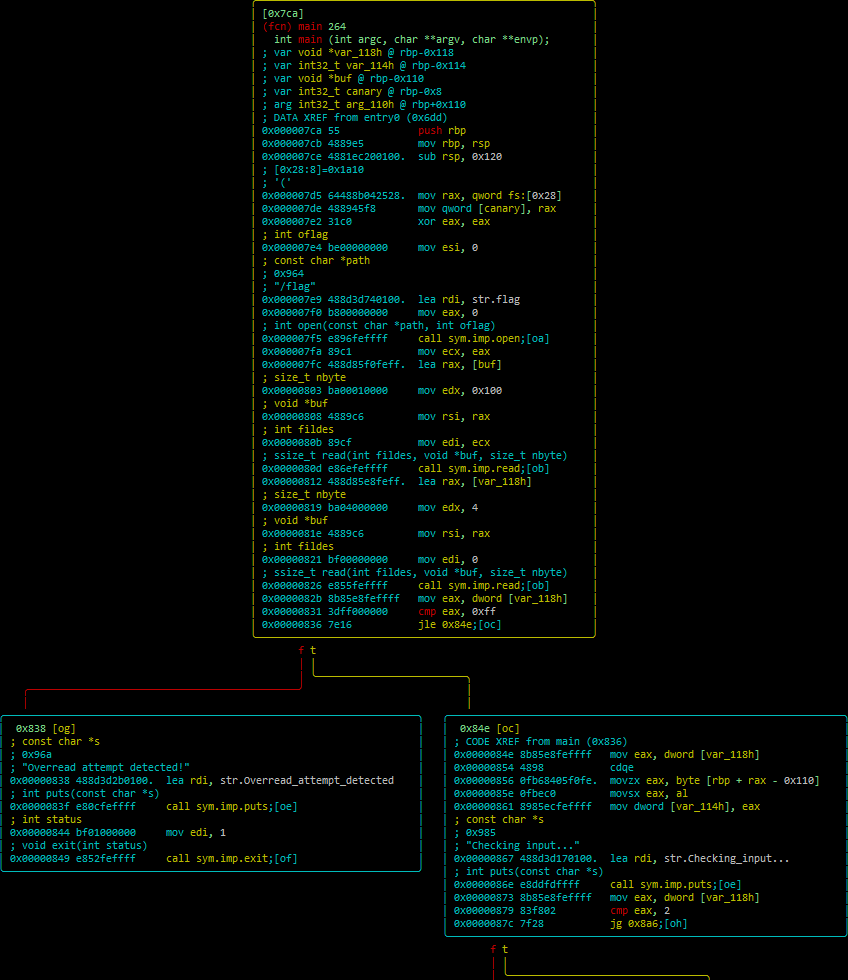
Headerquery turned out to be pretty simple. Here's the disassembly in a nutshell
The first block just opens the flag and reads it into a buffer. It then reads in 4 bytes from the user into a separate buffer. Immediately after, it compares the user's input against 0xff, with the size of input and comparison indicating that we're actually feeding in an integer. It then loads up the char from the array, checks if the integer is greater than two, and below (not in picture) either errors out if the index is greater than two or prints out your character.
Presumably, this means that we should only be able to leak out index 0,1 and 2. However, after some playing with the binary, it occurred to me that at any point in execution I could effectively leak the register value by simply making that register symbolic (due to how that function works as described above). With that in mind, i could leak any character i wanted out by simply setting the index, stepping until i got to the "checking input" puts call, making the eax register symbolic, then checking my constraints list. This is what I did, iterating through the indexes until I got the flag out.
OOO{memory_objects_get_you_every_time}- << Prev
- Next